Our Products
SCIMP: A Infrastructure Management Platform
SCIMP, Cosmic Kayka's Management Platform for Software Controlled Infrastructure, is your key to opening doors for innovation, network agility and optimization ultimately resulting in significant Return On your Investments. SCIMP facilitates device abstractions, definition and virtualization of network functions, orchestration of services and monetization of your applications and/or services.
The SCIMP Management Platform controls your Compute, Storage and Network Infrastructure through simple means: Collect, Analyze, Decision Support, Abstract, Configure, Optimize, Virtualize, Orchestrate and Monetize. The control is accomplished through a network of Software Controllers strategically positioned in the network. The controllers collaboratively view the whole network, gather stats, devise intelligence and use the knowledge to control the devices for optimal/efficient operation and/or transcend the knowledge down to the network devices periodically through its agents running on them.
Some of the features of SCIMP include:
- Software Defined Data Center (SDDC) Analytics for Enterprises, Carriers and Cloud Service Providers
- Data Center Console and Carrier Console
- Network topology detection (CDP, LLDP) and Advanced Visualization
- Alerts & Monitoring
- Reporting & Big Data Analytics powered by comprehensive data collection platform
- Detect traffic anomalies
- Traffic pattern analysis
- Device and System level performance analysis
- Predictive analytics
- Decision support
- Optimal network paths (various proprietary algorithms)
- SDDC Validation
- OpenFlow
- Device Abstractions through Metadata
- Network of Controllers controlling the devices with aggregate view
- Clearly defined Network Functions as Services
- Virtualization of Services
- Orchestration of Services, Resources and Interactions
If you are interested in SCIMP or need more information, Please register with us by clicking on the link below or simply send an email to the following address. One of our professionals will be glad to assist you and work together to help formulate a plan for your implementation:
customer.support@ckayka.com
Sound Off
SoundOff is a free messaging app with end-to-end encryption providing secure communications. The messaging platform provides multiple privacy levels to protect user privacy. The platform supports sending text, image and video content in the messages. It also supports attaching multiple document types including Word, PDF, Power Point, Excel, RTF, Text, etc., to the messages. The platform supports integrating with personal google drive to browse and attach documents to the messages. It also supports saving message attachments to the drive.
The SoundOff app also supports making app to app voice calls. The app runs on iOS and Android based phones and tablets.
customer.support@ckayka.com
Hurray! The Ubiquitous Platform - Is here already!!
Yes, you can believe it. Its here! The world's first of its kind and the long-awaited platform is just wrapping up trials with disparate businesses and users. We are proud to introduce the AI-powered Ubiquitous Platform to the world: It's omnipresent, universal, and far-reaching - with everyone, everywhere, all the time!
The mobile and online platform empowers users to connect and engage with the social space around them filled with family, friends, work colleagues, social communities and all the businesses around. Users can seamlessly engage with businesses everywhere from the mobile app just by tapping on the business. Sign up today and enjoy promotional calendar to manage your schedules. Great offers on video conferencing for your video chat and appointments! You can monetize on the Moonline™ platform. Yes, you heard it right. Put your skills into action, register as a service provider and start your micro business! Looking for a quality service, that is delivered to you on-demand? Just place a service request, sit back and relax while the service providers in your area compete/bid to get your business!
Moonline™ is introducing Tara™, our NLP agent. Platform users can engage with Tara™ to manage and book their appointments, pay their invoices, and shop for products and services offered by businesses, all executed with high confidence.
Moonline™ is the only messaging platform that empowers and attracts users and businesses into a common platform where all engagement happens. It provides a true presence for businesses by listing them where users spend most of their time. Users seamlessly connect, share and enage with service providers. Moonline™ empowers businesess with end-to-end digital transformation as a service.
The Moonline™ omnichannel platform empowers businesses of all sizes including Mom & Pop and Small-to-Medium Businesses to effectively reach customers, compete, and grow with affordable cost. The platform offers messaging-enabled, cloud-based SaaS toolset for businesses and equips them with a ubiquitous Mobile App and tools for Business Presence, Customer Care, Marketing, Branding, Promotions, E-Commerce (for both product and service offerings), Enterprise Messaging and Collaboration with Video Conferencing, CRM, Customer and Employee Loyalty, ERP, SKU-based discount pricing, Inventory Management, Operation Support Systems and AI-powered Enterprise Intelligence.
While digital transformation is out of reach for many businesses, Moonline™ is the one and only platform in the world that offers Digital Transformation as a Service (DTaaS): AI-powered Enterprise Intelligence as a Service, integrated Universal Communications as a Service (UCaaS), Enterprise Mobility as a Service, Hosting and Business Listing as a Service, Branding as a Service, ERP/CRM as a Service, eCommerce as a Service, Inventory Management as a Service, Invoice Management as a Service, Customer & Employee Loyalty as a Service, IAM as a Service, and Business Analytics as a Service.
The platform pulls together users to engage socially with each other and to connect with businesses around in what would be an ultimate platform of engagement and empowerment for users and businesses. Cosmic Kayka is in preparation to launch The Ubiquitous Platform. You don't want to miss the big event. Please check us out frequently to stay current on the launch and to be one of the first to experience it!
If you are interested in being the launch partner or an investor and would like to know more about the platform, please contact us at the email address below:
investor.relations@ckayka.com
RAGaaS, AI-powered Business Intelligence Service
As enterprises grew, so were their people, business units, operations, strategies, capabilities, technologies, products, services, processes, and more importantly the raw business information captured in multitude of information repositories surrounding every aspect of the enterprise. The enterprises are left with the question of how to tap into this huge information base and turn it into pure intelligence.
Cosmic Kayka is currently offering the solution with its RAGaaS product, an AI-powered Business Intelligence Service, to help enterprises turn their vast business information into pure enterprise intelligence. RAGaaS solution includes Tara, an AI agent equipped with enterprise intelligence, capable of accurately answering questions. There are a wide variety of use cases spanning Customer Support, Technical Support, Operations, Finance, Sales, Marketing, Contracts, Policies, Governance, Research, Training, etc., limited only by the type and amount of raw information an enterprise captures. RAGaaS uses a very powerful, adaptive, and dynamic RAG chunking strategy that offers a highly optimal solution with huge savings. The solution is highly configurable, provides unique tracing capability, and facilitates tuning during the prompt completion. The solution also facilitates user with the ability to use specific document or multiple documents to be used as a context for the prompt completion. RAGaaS is a proven solution even when the context is far from the relevant content with in a document let alone spread across multiple documents!
A $1.3T Asset Manager is faced with solving one of the most complex AI problems: when content is far from context, how does generative AI address the issues with inaccurate responses and the hallucinations. The asset advisors had to review vast number documents in order to accurately and effectively advise customers. The idea is to ingest these documents and feed them into a generative model that can answer questions from advisors with high accuracy. This is only a minor problem compared to the new congressional and SEC regulations the financial advisory companies had to abide by, especially as they are applied to Asset Management companies and their use of Predictive Data Analytics (PDAs) during the formative times. The regulations require demonstrative governance, transparency, and responsible AI measures in order to show the due diligence and fiduciary duties these companies are subjected as they advise to their customers. The asset manager have implemented POCs with OpenAI/ChatGPT, Vertex AI, Einstein AI while none came anywhere close to responding with accurate answers, let alone traceability, governance, and non-bias. RAGaaS rose up to the challenge and solved the very issue using its proprietary, highly optimal RAG solution. RAGaaS dynamic chunking strategy saves money, time and resources while facilitating optimal performance. The accuracy was so high, near 100%, that we recommended them to use RAGaaS performance/accuracy as a benchmark in evaluating other vendor proposed solutions. The traceability and transparency is inherent in the RAGaas solution where it is able to show how and why it gave a response the way it gave. The current popular models/vendors are just not able to provide traceability as is needed in this domain. RAGaaS, while being offered as a hosted service in the cloud, can also be deployed as an on-premise solution. Some of the feature highlights are listed below:
RAGaaS, while being offered as a hosted service in the cloud, can also be deployed as an on-premise solution. Some of the feature highlights are listed below:
- Adaptive framework
- Dynamic chunking
- Highly optimal while offering huge savings
- Supports various document types (PDF, Word, HTML, Text, etc.)
- Agnostic to distance between context and relevant content
- Ability to apply one or more documents for the context
- Ability to trace in detail how RAGaaS has arrived at the prompt completion and fine tune
- Integrates with Enterprise Information Repositories
- Integrates with Amazon, Azure, and Google Clouds
Enjoy the power of pure intelligence at your finger tips with RAGaaS!
Please contact our product team to arrange for a review of your enterprise AI journey and to evaluate how RAGaaS can help accelerate and augment your journey.
customer.support@ckayka.com
CCAM, Content-Conscious AI Model
As enterprises grew, so were their people, business units, operations, strategies, capabilities, technologies, products, services, processes, and more importantly the raw business information captured in multitude of information repositories surrounding every aspect of the enterprise. The enterprises are left with the question of how to tap into this huge information base and turn it into pure intelligence. However, the prelude to turning business critical information into enterprise intelligence is to identify the type of content the enterprise has and whether its worth looking into it. Depending on the size, an enterprise may have few thousands of documents to hundreds of thousands of documents. Manually reviewing thousands of documents and classifying them based on the content is a very time consuming and expensive proposition. The problem gets quickly compounded as enterprises carry legacy content let alone the content from M&A. Also, a typical M&A due diligence takes several weeks to months while the majority of time is spent on identifying and reviewing correct documents to make critical and timely decisions
Cosmic Kayka is currently offering an AI Model framework that enterprises can use to train on their own corpus and use the highly-effective model for classifying the content in production. The use cases span from classifying content whether its email messages, enterprise communications, customer contact messages to help route customer requests, to classifying unstructured documents whether they are contracts, compliance documents, business process documents, product and service-offering related documents, sales and marketing material, or training documents. The model is highly optimal with performance peaking at near 100% accuracy.
CCAM, the Content-Conscious AI Model, with its ability to effectively identify and classify content clubbed with RAGaaS ability to then turn important business information into pure enterprise intelligence is a true break-through solution all integrated from one provider. Some of the feature highlights are listed below:
- AI Model Framework
- Performs better than various traditional AI Classification Algorithms
- Highly optimal while offering huge savings
- Supports various unstructured document types (PDF, Word, HTML, Text, etc.)
- Ability to train and classify batches of documents together
- Ability to flag/alert any anomalies and/or misclassifications during training
- Integrates with Enterprise Information Repositories
- Integrates with Amazon, Azure, and Google Clouds
Being conscious of all of your content while critical, cannot be a humongous task. Enjoy the power of true conscious at your fingertips with CCAM!
Please contact our product team to arrange for a review of your enterprise AI journey and to evaluate how CCAM and RAGaaS can help accelerate and augment your journey.
customer.support@ckayka.com
Autonomous Enterprise, powered by Pure Intelligence
As we started looking deeper into the fundamentals of what is actually an intelligence, and even questioning whether the current state of Artificial Intelligence is considered intelligence at all. To bring more clarity, we asked more philosophical questions ourselves, that whether information, let alone knowledge (of information), is considered intelligence. It is those questions that started to shed some light into what is not intelligence more so than what is intelligence. In this thought experiment, we realized something more than ever before and beginning to understand what conscious is and got to our Eureka moment. And hence the birth of our CanC: Conscious, a non-biological Conscious. CanC is different from AI, in that it is pure intelligence. It is aware of, and in harmony with its surroundings. CanC is pronounced "Can-see".
CanC is our founder's dream project and we are all working harder everyday to make it a reality. Cosmic Kayka is currently building support infrastructure for CanC with Autonomous Enterprises being one of the first use cases. CanC uses world-knowledge from current AI models as it works in harmony with its surroundings. The goal is to generalize the support infrastructure so that it supports executing future autonomous tasks agnostic to whether they were issued by humans, AI agents, or CanC.
If you are impressed by our dream project and want to be part of our journey, contact our team to arrange for a discussion.
customer.support@ckayka.com
SPA: Security, Privacy and Anonymization Framework
Protect your customer sensitive data (PII) and enterprise business-critical data with SPA!
As enterprises grow, they soon start to outgrow their data privacy and security requirements. Also, the CIOs' efforts to streamline processes and drive business decisions on operational data insights in their effort to digitally transform the enterprise require a more comprehensive data strategy. Cosmic Kayka's SPA framework, with its comprehensive and extensive capabilities, addresses the core requirement and plays a central role in accomplishing enterprise data privacy and security. Cosmic Kayka is currently offering packaged solution for Postgres with integration support. SPA is also available as a custom solution for MySQL, MS SQL Server, and Oracle databases as the framework is independent of any specific DBMS.
SPA is self-contained and is entirely independent of any other extensions nor does it rely on specific DBMS's features such as Security Label implementation of postgres. SPA has its own rule system. However, it can be integrated with any custom privacy functionality including third-party extensions. SPA is a novel solution in that it is a framework, dynamic, rule-based, fully configurable, supports rule inheritance, applied in-database (i.e., no latency as is typical with proxy or streaming based solutions), and has the ability to morph data based on who is accessing the data. It is because of its flexible framework, and dynamic (query-time) nature, SPA is best suited for Data Security and Privacy. Some of the feature highlights are listed below:
- A Framework for Security, Privacy and Anonymization
- Rule-based framework
- Highly flexible and easy to extend
- Multitude of privacy and anonymization functions
- Ability to mask partial segments or mask fullly, obfuscate, encrypt, fake, anonymize, transform various data elements such as: first name, last name, date of birth, social security number, work and personal phone numbers, email addresses, street address, state, zip code, salary, strings, numbers, dates, money, etc.
- Default stock implementation for various masking, obfuscation, encryption, and anonymization functions
- Separation of masking from obfuscation
- Ability to override default implementation using rules
- Comprehensive rule types with ability to set fixed values, NULL, or use custom functions
- Ability to scope rules at user level, role level, role group level, or for all users (PUBLIC)
- Support for rule inheritance via role inheritance. NOTE: Only one rule that gives most access (or least privacy/anonymization) is applied, when in conflict
- Support for applying privacy and anonymization to new views using spa functions
- Auto enable existing tables and views for privacy and anonymization
- Support spa-replication while applying privacy and anonymization during replication
- Default functions to support auto enabling of existing tables and views for 20+ data types
- Support for custom functions with arbitrary number of input parameters and data types
- Support for both static and dynamic masking and anonymization
- Fully configurable enabling total customization
- Integrates with custom implementation and/or a third-party anonymizer
- Supports all major versions of PostgreSQL including open source Postgres, Amazon RDS, Amazon Aurora, Azure database for PostgreSQL, EnterpriseDB
Enjoy your privacy, feel secure, and hide your sensitive data behind SPA!
For more information on feature highlights, supported DBMSs, and comparison with other products, please download product data sheet for SPA here: Download Product Data Sheet
Please contact our product team to arrange for a review of your enterprise data privacy and security needs and to evaluate how SPA can help secure your enterprise data.
customer.support@ckayka.com
Enterprise Link
As organizations are moving towards digital transformation, the first and foremost on the minds of CIOs is to tackle inefficiencies in organization and team communications, and to do so in a highly secure manner protecting ip and critical information. The other important aspect in digital transformation is to equip the sales and marketing teams with information on the go while they are interacting with potential customers off premises.
Cosmic Kayka offers solutions to enterprises eager to take that big step of digitally transforming their business. E-link is a white-label end-to-end messaging solution for enterprises based on Cosmic Kayka's SoundOff mobile platform. The app runs on iOS and Android devices. It facilitates secure corporate communications at enterprise, department and team levels. E-link supports integration with enterprise document repository and allows users to send, receive and save various document types including Word, PDF, Power Point, Excel, RTF, Text, etc. E-link supports end-to-end encryption and offers various privacy levels and safeguards for business critical communications. The employees can connect to the repository from the E-link app on their mobile device, and share or present at customer premises.
Please contact our product team to arrange for a review of your enterprise messaging and security needs and evaluate how E-Link and C-Shield can help secure your enterprise communications and systems.
customer.support@ckayka.com
Quantum-proof Cyber Shield (C-Shield™)
with Proactive identity Protection (PiP™)
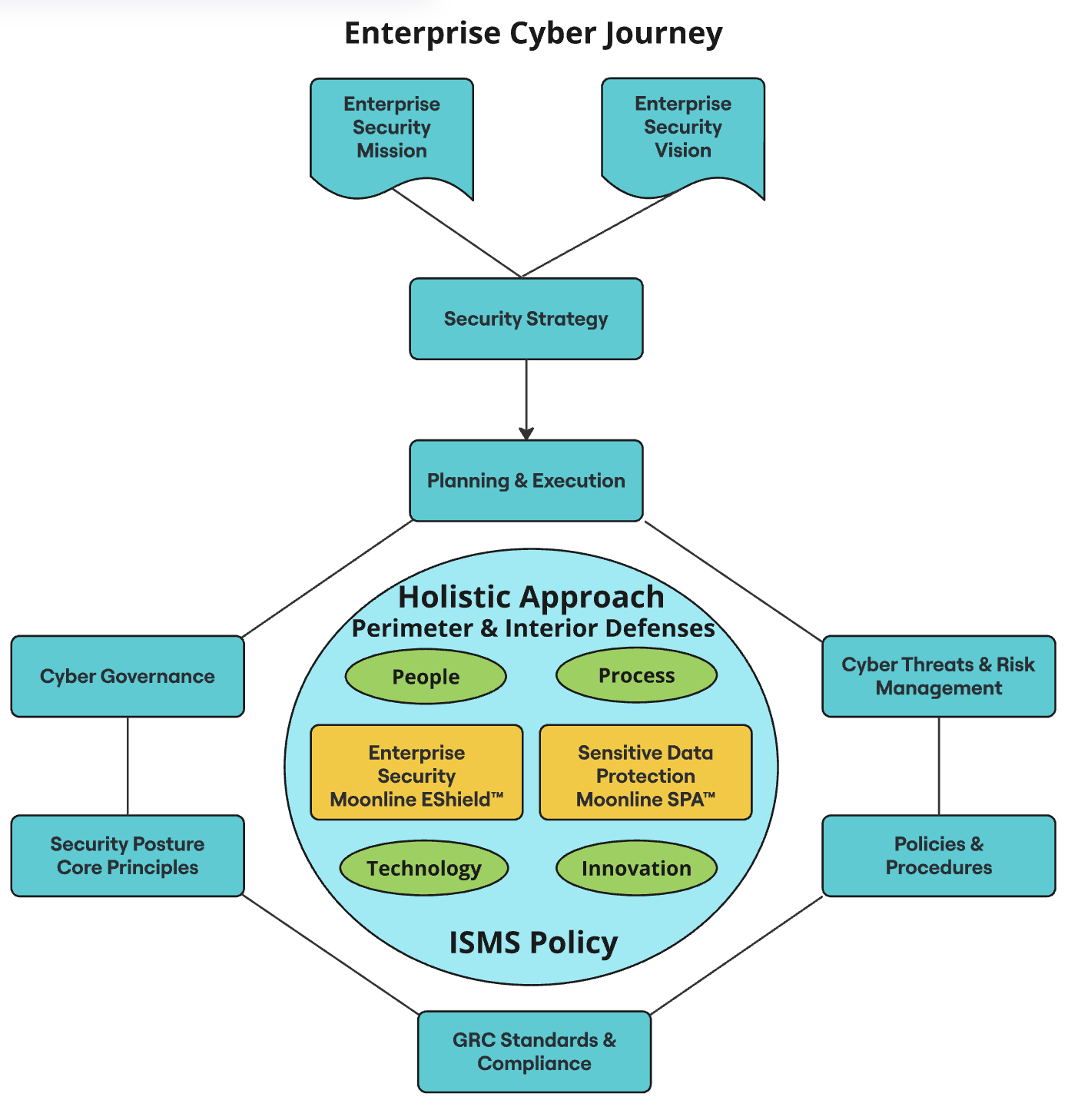
According to the SANs survey in February 2016, over 88% of the enterprises ranked Access and Authentication as their top most priority and hence is the area of their top most spend in Enterprise Security. With ever increasing cyber threats, authentication, access, and application security are the top 3 areas of concern for enterprises. Protection and Prevention is the top most strategy at 72% of the enterprises to address these concerns. It has been almost a decade, and yet there are more and more security breaches halting enterprises, stealing both customer-sensitive and business-critical data. The CIOs and CISOs have increasingly taken a safe stance in their decision making when chosing major well-known vendors as capable security solutions vendors with a false hope. Despite big claims and security guarantees from major security vendors, we see almost every major sector is getting hit across the world. It is evident that the hacks are more sophisticated than the solutions offered by the major vendors to protect data and systems. You are not alone in this regard. We recognize that we are a small company, but we have the most innovative and novel solutions architected by our pioneers. Few of the executives starting to change this trend by aggressively nursing a culture to not get locked in with one well-known major vendor rather identifying vendors with innovative solutions in specialized areas irrespective of their size. The C-Shield innovative solution focuses on these top 3 areas of concern for enterprises while its product strategy is also aligned with protection and prevention.
Enterprise Shield offers enterprise security by providing secure access to Enterprise Applications, Application Servers, Database Servers, Network Servers, Desktops, and Devices. The proprietary solution is impeccable, uses our security trade secrets, and is highly difficult to breach as it uses phone as a dongle coupled with software. It is highly effective compared to prominent authentication mechanisms as we have seen numerous break-ins despite the claims of, for instance, how secure the multi-factor authentication (MFA) methods are. Here is an analogy: In 2-factor authentication, the act of login with valid credentials (factor 1) triggers a second (factor 2) authentication mechanism using methods like email, OTP, etc., but these mechansims are also the target of sophisticated hacks, let alone providing a means for malicious users to hack the credentials and/or cause disruptions through locking out user accounts. You would see how both the active and passive MFA mechanisms are triggered after-the-fact, lazy, and reactive in nature compared to a proactive prevention strategy used by C-Shield. Other, more secure means such as U2F, UAF, FIDO, FIDO2 have similiar issues with phishing, higly complex setup, and expensive to implement. The C-Shield solution makes impersonating a person, email, website moot, i.e., it is phishing-proof. The C-Shield solution is highly secure, more practical, easy to configure, and less expensive as well compared to SAML and OpenId Connect for the SSO implementation to access web applications. The C-Shield supports all 5 factors for authentication (Knowledge, Inherence, Possession, Location, and Time) while securing them with proactive strategy.
C-Shield thwarts brute force hacking attempts quickly. The effect is reduced future hacking attempts serving as a prevention. First, it makes it nearly impossible to crack a password. Second, even in the event where a hacker guesses a user's password, the hacker is still prevented from accessing the systems. Third, there are no recovery phones or recovery emails nor are there OTPs involved in the solution as these are the vehicles the hackers reset once they hack into authentication databases. In fact, several of the recent hacks in the Healthcare and Banking sectors included resetting of the recovery emails and recovery phones to prolong the time they needed to steal the sensitive information.
Moreover, it is not practical to expect enterprises to modify their existing access and authentication software to implement a new solution. Migrating hundreds of systems and applications to adapt to any new solution costs time and money let alone the risk of downtime to production systems. In medium to large enterprises the cost of migration combined with its impact to production systems is much more than the cost of the actual solution. We understand the criticality of this aspect and designed the solution with minimal impact. The C-Shield solution does not require any modifications to enterprise's existing security frameworks, authorization flows, APIs or systems. The solution is entirely self contained and doesn't require any migration or adaptation.
C-Shield prevents MFA Fatigue by 99.9999999999998% compared to FIDO2 that has been regarded as the most secure to date. It prevents MFA Fatigue by 100% when Precision Proximity factor is used. All prevlant security solutions are subjected to account lockouts as malicious users attempt to hack-in while C-Shield solution prevents account lockouts 100%. C-Shield security solution is also future technology proof. With exponential advances in quantum computing research, its critical for enterprises to chose a security partner that is aware of such risks. While FIDO2 uses key pairs that are prone to compromise from quantum computing technology, C-Shield uses a higly-secure, protocol-based, quantum-proof algorithm protecting access to systems. C-Shield also protects encrypted passwords from quantum compromise and quickly averts attempts to crack passwords. Enterprises should carefully review present security strategies, and ensure adequate measure are in place to protect enterprise systems and resources from risks posed by future technologies, specifically quantum computing.
The cyber-attacks on enterprises have skyrocketed leading to monetary, trust, and reputational damages. The attacks have incapacitated enterprises and rendered them vulnerable to huge ransoms. With over 2000 breaches per day under the protection of prominent vendors like Microsoft, Google, Okta, Ping Identity, Cyber Ark, Sail Point, etc., the enterprises are still going deeper into the rabbit hole under the false hopes from these prominent vendors. We wondered what is going on and after thorough research have identified the root cause of these breaches: it is the vulnerable standards and vulnerable implementations. If a malicious user can breach systems by simply phishing credentials or impersonating, then the Identity is basically Unsolved! The C-Shield Proactive identity Protection (PiP) solution addresses various vulnerabilities with 2FA, MFA, OTP/TOTP, Passkeys, U2F, UAF, FIDO2, WebAuthn, SAML, OpenId Connect, and renders phishing attempts futile. The impeccable C-Shield, perhaps, is the most secure solution in the world!
Here are some of the salient features of Moonline C-Shield solution that is more secure and practical than 2FA, MFA, U2F, FIDO2:
- Proactive identity Protection (PiP™)
- Phishing proof
- Quantum-compromise proof
- Zero Trust
- Zero Code (with minimal integration)
- STRIDE-proof, also supports FIDO2
- Threat Detection and Response (DaR)
- Numerous Security Policies
- High Interoperability
- Cost-effective and Optimal Solution
- Compliance & Governance
- Impeccable Defense
C-Shield helps enterprises in defining a security posture that plays a vital role in enterprise readiness for cyber threats. The C-Shield strategy is more secure compared to passive implementations of FIDO2, U2F, CBA as it uses user's mobile phone as dongle coupled with its Proactive identity Protection strategy. The following is an enumerated list of security policies C-Shield supports:
- KP - Keep your Password
- KPX - KP Extended
- KPX2, KPX2' - KP Extended 2
- DP - Dynamic Password
- DPX - DP Extended
- DPX2, DPX2' - DP Extended 2
- PL - Password Less
- PLX - PL Extended
- PLX2', PLX2'' - PL Extended 2
- CA - Continuous Authentication
- CAX - CA Extended
- BTE - Blue Tooth Enabled
C-Shield seamlessly integrates with your current security infrastructure while enhancing your enterprise security needs and capabilities. The C-Shield can also act as an additional guard better protecting your existing security solutions, whether they are homegrown or through another IdP, with an impeccable proactive defense against cyber threats.
- Shield internal or 3rd-party Identity Provider (IdP)
- Shield Legacy Apps
- Shield Modern Apps
- Shield 3rd party SaaS Apps
- Shield SSO with PiP
- Shield Social Login
- Shield App Servers and DB Servers
- Shield Network Resources
- Act as your Enterprise IdP
C-Shield offers a holistic solution with a combination of perimeter defense and interior defense. The perimeter defense focusses on securing access to the systems and resources while the interior defense focusses on securing customer-sensitive and business-critical data in the unlikely event of a breach to perimeter defense so that the data is still protected. The impeccable interior defense is provided by our product called SPA, a Security, Privacy and Anonymization Framework. It protects your customer sensitive data (PII) and enterprise business-critical data with a rule-based, in-database, dynamic framework. Please check out details on SPA security and privacy framework from the product list.
For more information on feature highlights, security posture, associated policies, and comparison with other products, please download product data sheet for Moonline™ C-Shield™ here: Download Product Data Sheet
Please contact our product team to arrange for a review of your enterprise security needs and to evaluate how C-Shield can help secure your enterprise systems and resources. White-labelling and custom implementation options are also available.
customer.support@ckayka.com
Student Link
The top two missions of a school are to reduce the student drop out rates, and to increase the graduation rates with measurable high student learning. Numerous researches are showing that the number one reason why schools are not able to achieve their mission with ease is due to the lack of early identification and lack of strategies in increasing student engagement during the course of the programs.
StudentLink is a white-label messaging app targeted for schools and universities to help accomplish their mission. While the messaging app is full of rich features that facilitate social communications among students at underlying schools, it also facilitates organized communications at University, Department and Course level faculty-student communications. StudentLink also supports communication with in internal organizations such as University Center, Tau Beta Pie, Alpha Beta Omega, International Students Association, Campus Housing and Campus Jobs.
We understand the key to successfully accomplishing schools' top mission is to break out of formal methods of student communication into where students are naturally like to have their social communications. The idea is to increase student engagement by being an integral part of their day-to-day social communication vehicles, aka, messaging apps. The StudentLink messaging app facilitates course level communication between faculty and students whether its communicating about what will be covered in the upcoming class or communicating assignments, grades, reference materials or even alerting students about upcoming due dates. But, more importantly, the app serves as a social link to students, breaking the direct-link-to-students barrier.
The StudentLink also integrates with schools' ERP systems to identify enrolled students and automatically determine student eligibility for various departmental, course level and subscription-based messaging groups maintaining the integrity of communications.
Please contact our product team to arrange for a review of your school's student communication and student engagement programs and how StudentLink can help improve student engagement and ultimately improve learning outcomes.
customer.support@ckayka.com
Hospital Link
Every hospital network's mission is to provide competent, innovative, and exemplary care services for its patients. The stakes are much higher than ever to increase the efficiency of ED and other departments. We understand efficiency means delivering the right care effectively and efficiently, keeping the patients and families well informed through out their stay. It is critical to empower case managers with top notch tools so that the care is effectively managed as they play a vital role in meeting the challenges. Moreover, the demand for high performance in an ED setting is more evident as the penalties for ineffective or inefficient performance are far greater.
H-Link is a white-label messaging app targeted for Individual and Network Hospitals to help accomplish their mission. The messaging app is full of rich features facilitating communications and empowering Case Managers and Care Teams to provide utmost and efficient care through sharing of information. The app supports end-to-end encryption and offers secure messaging via multiple privacy levels.
With H-Link the case managers and care teams can operate with a more synchronized plan of care that spans interdisciplinary care coordination. The ED flow rounds would be much more effective with H-Link by keeping the entire care team and the admitting physician on the same page. The H-Link supports vital communications throughout the process of admission, providing care, transition and discharge.
The H-Link also integrates with hospital's ERP systems to identify and automatically determine eligibility of members (from various interdisciplinary departments) for the underlying messaging groups to maintain the integrity of communications.
Please contact our product team to arrange for a review of your case management needs and to evaluate how H-Link can help accomplish your hospital network's mission.
customer.support@ckayka.com
Notification Link
In the mobile app world, customer retention is a factor of times harder than new customer acquisition. Organizations are realizing this and allocating significant portion of their customer acquisition budget to customer retention efforts. While steady influx of unique features, improved user experience and creating excitement among user base on a regular basis are great first steps, its still a challenge to get the users back to the app on a regular basis.
Push Notifications is the key to the challenges faced by various organizations to improve customer retention. Notification messages pushed to the users can convey new features, improved user experience and exciting engagement initiatives to the users. Targeting notifications is crucial for an effective campaign while it is also economical.
Cosmic Kayka offers Push Notifications as a Service via its Moonline™ platform which comprises of an app tool kit, a notification center, a provisioning and dashboard portal. Moonline™ supports notifications with text, image and video content. The provisioning and dashboard portal is an easy to use web portal where partners can register their app, provision notifications, define logistics and check out the performance reports. The platform can also help increase new customer acquisition converting leads to actual customers through web push notifications.
Please contact our product team to arrange for a review of your customer retention plans and how Moonline™ can help accomplish your customer retention and new customer acquisition goals.
customer.support@ckayka.com
MPPharma
MPPharma is a Big Data analytics platform supporting supply and demand forecasting of prescription medications for Insurance and Pharmaceutical industries, track disease onset & progression and provide helpful insights to CDC, physicians and patients around the world.
The platform is powered by our convergence algorithms that focus on market population, potential target segments, current and historical data. The platform is capable of processing billions of health records to produce business critical information in "ER" critical speed. MPPharma is an easy to configure platform with virtually no limit to the number of diseases, stages, or the number of drug formularies.
MPPharma uses Hadoop, Linux, JAVA, Web Services, XML and XSLT technologies, follows the Clinical Document Architecture (CDA) specifications and supports both Continuity of Care Document (CCD) and Continuity of Care Record (CCR) formats.
If you are interested in MPPharma or need more information, Please register with us by clicking on the link below or simply send an email to the following address. One of our professionals will be glad to assist you and work together to help formulate a plan for your market research and/or implementation needs:
customer.support@ckayka.com
